Compatible Operating System
Compatible Operating System: › Operating systems (workstations): Windows XP SP2 or higher, Vista, Windows 7, 8, 8.1 and 10. › Operating systems (servers): Windows Server 2003 SP1 or higher, 2008, 2008 R2, 2012, 2012 R2, 2016 and Server Core 2008, 2008 R2, 2012, 2012 R2 and 2016. › Internet connection (direct or through a proxy )
Features
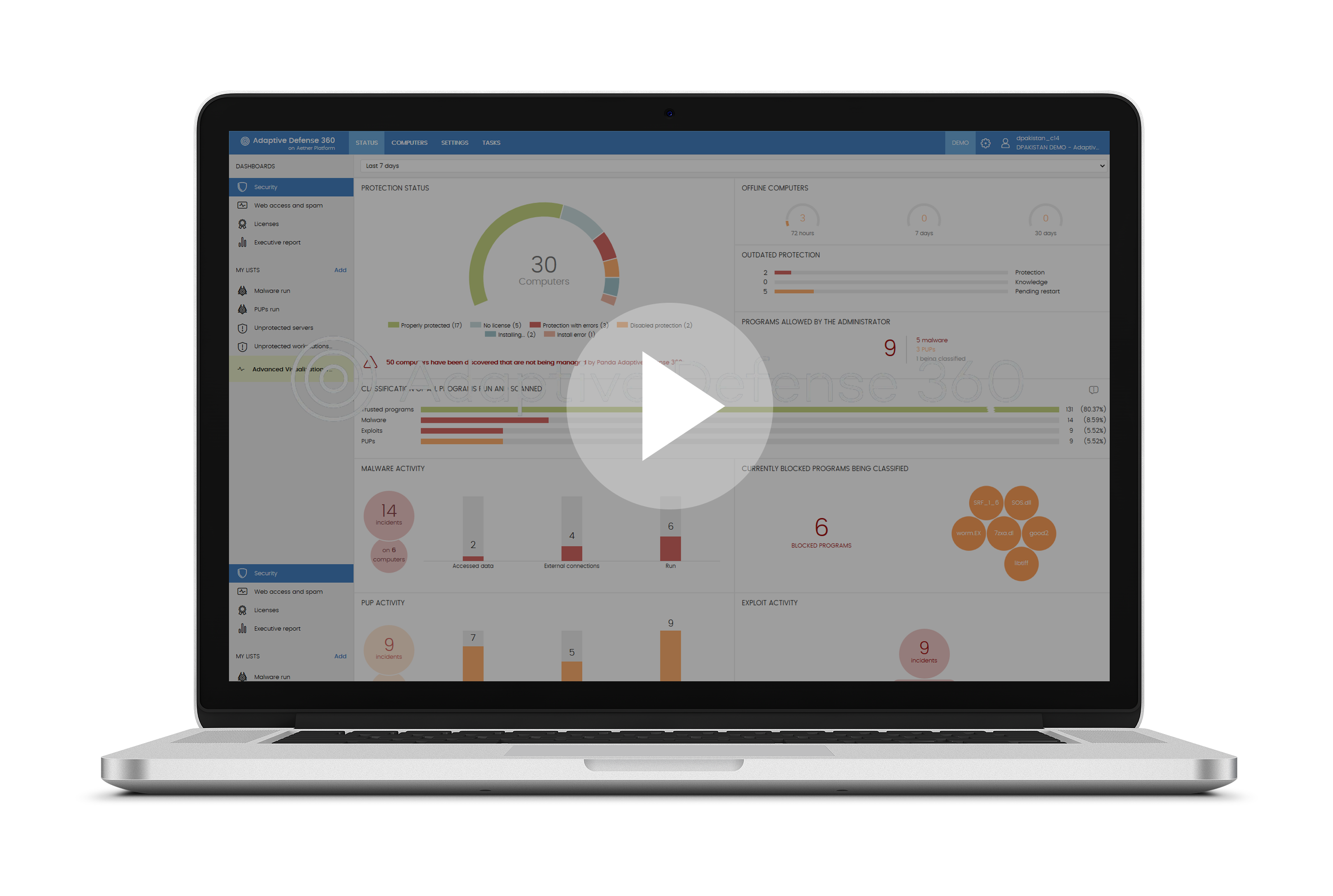
A New Cybersecurity Paradigm is Born. Panda Adaptive Defense integrates EPP and EDR capabilities, with 100% Attestation and Threat Hunting Services, all delivered by a single light agent
Web Protection/URL Filtering
Blocks access to dangerous sites and protects computers from malware downloads, block Facebook, YouTube etc. Block Internet if User switches to Browser Based VPN like Zenmate
Device Protection
Prevents or limits the use of peripherals connected to the user’s computer to prevent Data Leakage/ Infections from external devices such as USB flash drives, Mobile, Modems etc. Allow only authorized Devices to use on a group of Computers
File Protection
Blocks execution of files classified as viruses, unknown items, grayware, etc.
EDR Protection
Blocks execution of untrusted files. Block Exploits and Advanced Persistent Threats (APT).
Continues Monitoring
Continuous monitoring of files and processes: Constant monitoring of 100% of executable files
Forensic Analysis
Audit Mode provide GUI Forensic Activity to access the scope and impact of an infection in SANDBOXING environment.
Big Data and Machine Learning techniques
Big data of signatures for all Malware intercepted. Panda Collective Intelligence is also part of it, which gives you signature of new malware (Trj CI.A) in just 5 Minutes
Dynamic Exploit Detection
Maximize your protection with the new anti-exploit detection technology. we have expanded our protection and containment technologies with a new dynamic and adaptive anti-exploit technology. This new module follows the adaptive defense protection model based on continuous process monitoring
Behaviour-Based Detection
The vulnerability protection module in Adaptive Defense 360 uses contextual and behavioral rules to ensure companies can work in a secure environment even if they have systems that are not updated
Classification Of Processes By Panda Experts
Spam and Antivirus for Exchange Server
Security against unauthorized protection tampering
Isolate compromised Computers
Every 6 Seconds , 11 Digital Monsters come looking for you
Watch Video
Interactive demo request
A New Cybersecurity Paradigm is Born. Integrated Endpoint Protection Platform, EDR and 100% Attestation Service